SouthBridge Consulting Blog
Think about how happy you are when you first get your new phone. If you are like most of us you can’t keep your hands off of it. You try all the new features out and mutter to yourself, “wow, this is so cool”. The enthusiasm that people have for their new mobile devices can be a major benefit for the company they work for, too. Today, we are going to discuss how, with all the features and powerful computing power, you can work effectively on your smartphone.
As much as we hate to admit it, the first thing that many people still think of when they hear the term “tech support” is the experience that comes with an antiquated approach to technology services: the break/fix method. Fortunately for us, we are seeing many businesses make the better decision, and turn to the clearly superior option, managed IT.
The modern business has to deal with a lot of potential security problems. Today’s threat landscape is filled with people looking to prosper off of your misfortune. As a result, doing what you can to maintain the security of your network and data is essential. Today, we will discuss how maintaining your organizational cybersecurity doesn’t have to be costly or time consuming.The best way we’ve found to go about doing this is by highlighting a few key actions that you can take to keep your network secure and your data safe.
Windows 7 might not be supported by Microsoft any longer, but millions of people are still using PCs that run the antiquated operating system. Since Microsoft has put an end to extended support for Windows 7 OS, a couple bugs have been found. Let’s take a look at what exactly is behind these issues and discuss your options.
It wasn’t too long ago when the idea of video conferencing was a very complicated one. The technology just wasn’t there to make it a major benefit for companies. As conferencing technology has been innovated upon, however, it now presents a laundry list of substantial benefits. Let’s take a look at some benefits you can see by moving to video-driven meetings.
Augmented reality has been one of the most cited emerging technologies for the past few years. It was the technology that was supposed to fuel Google Glass, the failed attempt at creating a pair of revolutionary smart glasses. Since then, there hasn’t been much press about AR in the mainstream media and not much is known about major tech companies’ attempts to improve AR technology.
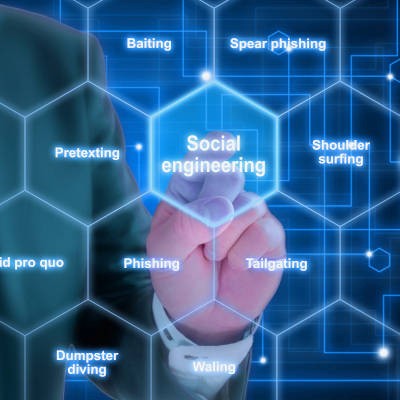
As prevalent as cybersecurity threats unfortunately are today, many users tend to overlook major threats that they just aren’t focused on nearly as much: social engineering attacks. Social engineering attacks are just another means for a cybercriminal to reach their desired ends, and therefore needed to be protected against.
How often do you find a message in your SMS inbox that has clearly come from a business, but you almost have to wonder, simply because the incoming number seems to be randomized? Google has taken notice of this challenge, and so has rolled out a means for businesses to confirm that they are in fact the ones sending a particular message.
Microsoft has a well-developed reputation for creating software that enables users to achieve their work objectives, especially in the business setting. Here, we’re diving into a few capabilities of one such software title, OneDrive, to review some of the features that a user might want to take advantage of.
The curious thing about information technology is that, while it improves as any other technology would, the environment can accelerate the various changes made to it at various rates. As a result, knowing when your business needs to upgrade its technology isn’t always so cut-and-dry. To help, we’re sharing a few clear indicators that hint that the time has come.
IT administrators are pretty particular about what software is used on the networks that they manage. This is not because we have any vested interest in the software itself, it’s because of the inherent reliability of the software they manage. They’ve tested it, they manage it, they know it. When an organization starts dealing with employee-downloaded software--especially if there is no procedure in place to report additions to IT--they can quickly lose control over the network.
Wi-Fi has swiftly become one of those amenities that we just expect to have, including in the workplace. While it does make work around the office more convenient, it should not be at the cost of your security. To help prevent this, we’re reviewing a few key Wi-Fi security considerations to keep in mind.
Improvements in technology have allowed us to come a long way since the days of our ancestors, which is made exceptionally clear by our developments in the realm of healthcare. There are so many ways that healthcare providers can use information technology to their advantage, so we’ll cover a select few here.
We hear a lot about the benefits of moving your business to the cloud. It can reduce that big expense on new infrastructure and the ongoing management costs. The cloud can increase the effectiveness of your IT budget. It can add functionality and increase user satisfaction.
Businesses are rapidly moving all or portions of their IT to the cloud, and for a lot of good reasons, but before you do, it is important to remember the following: