SouthBridge Consulting Blog
When security breaches and data breaches are mentioned in the same breath so often, it’s easy to look at them as one and the same. However, we want to take a moment to explain the differentiating factors between the two, as it could be all the most important for protecting your business in the future.
We talk a lot about different types of technology, securing your technology and your accounts, and a lot of other technology-related issues on this blog, but because of the generalities of whatever technology (or strategy) we’ve chosen to write about that day, we never confront the thing that is most important to a business: How does any technology fit into what we do here? What value do we get from any type of technology? Today, we thought we’d talk a little bit about what you need to do to find the right technology for your business and how to come up with those decisions.
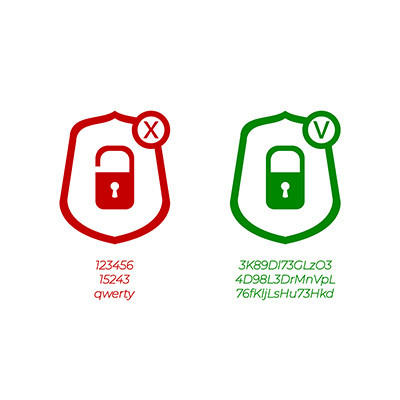
Simple passwords are just not an effective security practice, so if you’re still using credentials like Password, 123456, Guest, or Qwerty, listen up. You need better password hygiene practices before you suffer from a data breach. Here are some ways you can make a better password to protect your business from threats.
There’s no beating around the bush with this one; moving data from one place to another, also known as data migration, is critical to get right the first time. If you create and follow a migration strategy, evaluating here and there to make sure it’s all going according to plan, you’ll see great success in this effort. Let’s go over how you can make it happen.
When times get tough, businesses are pretty quick to start cutting costs wherever they can…and frequently, the business’ IT is the first thing to hit the chopping block.
While we contend that IT is the last thing you want to cut back on when times are tough, you may not have a choice. Therefore, we wanted to take a few moments to explore how you can resist some of these cuts—and if not, what you need to prioritize.